HSTS¶
This page will show you steps to configure HSTS (Strict-Transport-Security) response header for your site. Refer this MDN link for more details. HSTS response header informs browsers that the site should only be accessed using HTTPS, and that any future attempts to access it using HTTP should automatically be converted to HTTPS.
When a browser knows that a domain has enabled HSTS, it does two things: - Always uses an https:// connection, even when clicking on an http:// link or after typing a domain into the location bar without specifying a protocol. - Removes the ability for users to click through warnings about invalid certificates.
Note: For demo purpose, we will be using www.nviztest.com domain as an example.
Prerequisite¶
- You must have a domain configured on Nitrogen.
Steps¶
-
Click on
Securitymenu, and openHSTStab. -
You will be taken to screen to provide details.
-
Max Age: Time for which browser will remember that site should be accessed with HTTPS secure connection.
Note: We recommend keeping it 1 year. -
Apply to all subdomains: Should this setting be applied for the requests to the subdomains as well. Note: We recommend keeping it enabled. -
Allow browsers to preload: For a user to take advantage of HSTS, their browser does have to see the HSTS header at least once. This means that users are not protected until after their first successful secure connection to a given domain.
Google maintains a list of domains that are to be accessed securely. All major browsers refer it. Therefore, if preload is enabled, even the first request to the domain will be secure. Note: For this to work, you will need to add your domain to HSTS list here.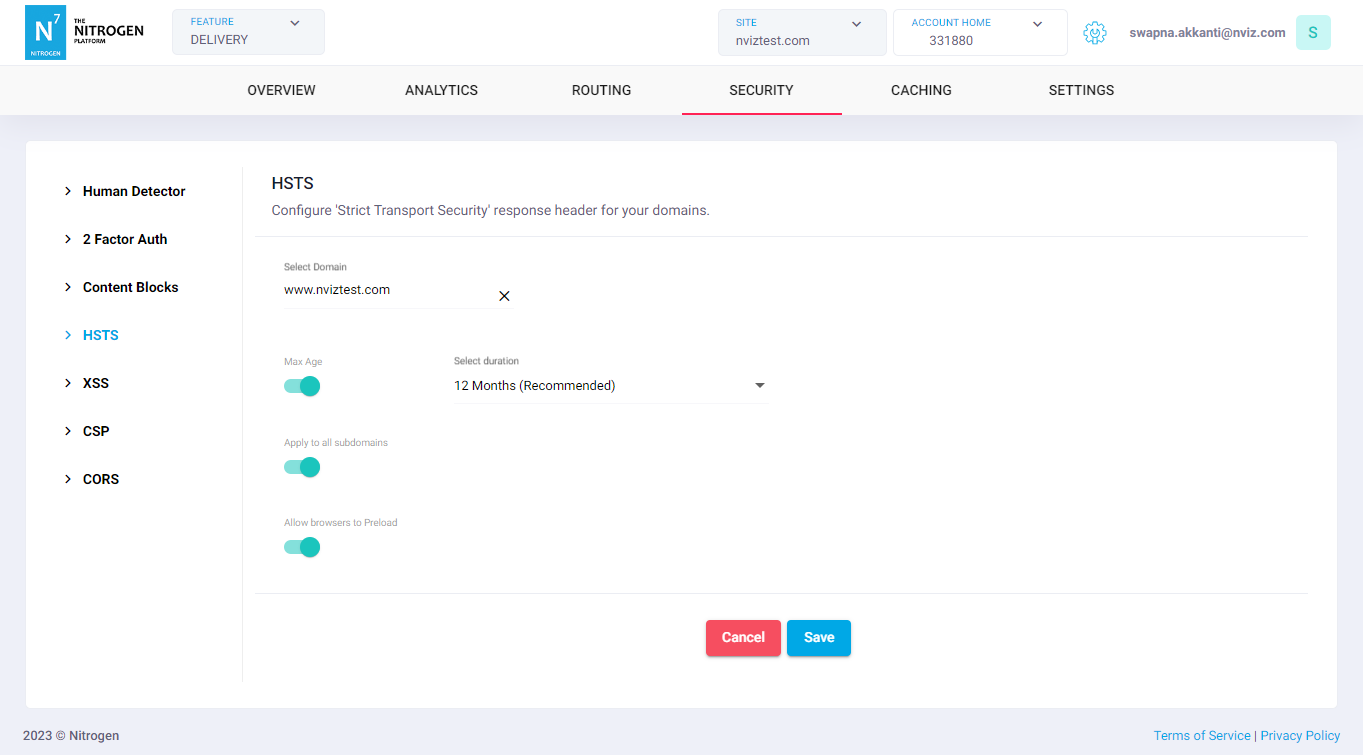
-
-
Click on
Savebutton.
Notes¶
These changes will only take effect when deployed. Saving them will only be saving them in draft. Please refer documentation about Deploy process for it.